Early last year I started a blog post about the preparation for Red Hat Certified System Administrator (RHCSA) exam. My intention back then was to have more posts follow suit about the exam topics. Like many things in life, things don’t always go according to plan. That was the only post, but I passed the RHCSA exam.
Today, I’m going to start another new post about the preparation for the Red Hat Certified System Engineer (RHCSE) exam. I already booked an exam which is taking place on September 12. The exam is 3.5 hours long and cover a broader range than before.
Let’s start with recovering the root password on RHEL 7 or CentOS 7. Most of us probably know that we could achieve this with the following steps:
- Start by passing the
rd.breakoption to the kernel command line starting withlinux16in the Grub menu entry. - Remount /syroot
- Set the root password
- Relabel all files including the
/etc/shadow
On my test VM running CentOS 7, I encountered this problem after doing the first step:
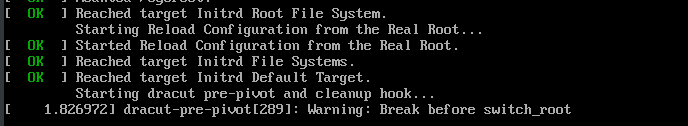
According to this Bug 1031015 report, this happened because of the order of console=tty0 and console=ttyS0,115200 in the kernel command line (which in turn generated from /etc/default/grub). If you’re curious, check out that Bug 1031015 for more details. So, for me, I need to make sure the order of the console is as the following: console=tty0 console=ttyS0,115200 rd.breakor just get rid of console=ttyS0,115200 completely.
Remount the /sysroot as read-write
switch_root:/# mount -o remount,rw /sysroot
Swith into a chroot jail, where /sysroot is treated as the root of the file system
switch_root:/# chroot /sysroot
Set a new password:
sh-4.2# passwod root
Mark all files (including the /etc/shadow) to be relabeled during boot
sh-4.2# touch /.autorelabel
Exit twice and reboot.
Alternatively, we can also set the root password without relabeling all the files according to this blog post by certdepot.net. The idea is that, we set an additional option to the kernel command line: enforcing=0 to set the SELinux in permissive mode. After remounting the /sysroot and setting the root password, don’t reboot yet. Open a new console, and run restorecon on /etc/shadow. It does make a lot of sense and is a very cool solution.
You can read more here: https://www.certdepot.net/rhel7-interrupt-boot-gain-access-system/